Fake Security Update Message Installs Flubot Banking Malware
- Admin
- Nov 4, 2021
- 2 min read
Published: November 02, 2021 on our newsletter Security Fraud News & Alerts Newsletter.

In our online world there’s an endless supply of information we depend on to shop, work, and explore ‘til our heart’s content. But within that, another world exists; one where cybercriminals try their best to exploit unsuspecting and trusting users. And when no opening exists, they create one, and that’s where Flubot banking trojan enters. Thanks to a Twitter post by New Zealand’s CERT NZ (computer emergency response team), we now know bogus Flubot security warnings are the latest ruse to install the malware on Android devices.
New Zealand’s CERT NZ tweet gives us a front row seat to how Flubot’s malware is being downloaded, and how the right response can keep us from becoming the next Flubot victim.
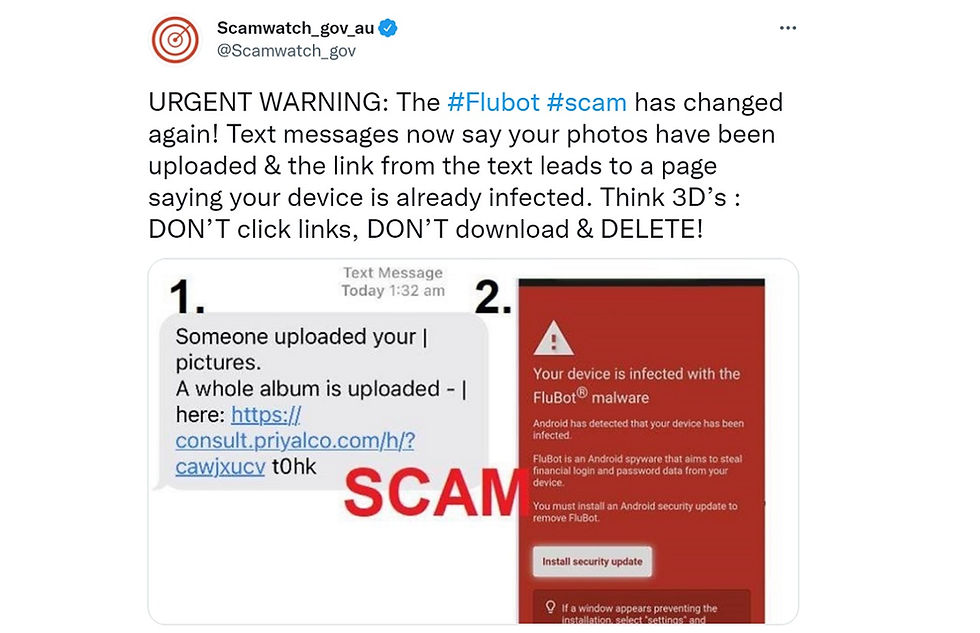
How would you respond to this message on your Android device?
“Android has detected that your device has been infected. Flubot is an Android spyware that aims to steal financial login and password data from your device. You must install an Android security update to remove Flubot.”
CERT NZ’s response: “If you are seeing this page, it does not mean you are infected with Flubot. However, “if you follow the false instructions from this page, it WILL infect your device.” Adding “…if you see this page close the page IMMEDIATELY and DO NOT click “Install security update.” According to CERT NZ, this is currently the best and safest response to the bogus Flubot security update.

Flubot’s Brief History
A relatively new banking trojan, Flubot has been infecting devices since late last year. Also known as Cabassous and Fedex Banker, Flubot has been actively stealing data like payment information, banking credentials, contacts, text messages, and more from infected devices.
Before this latest security update ruse, Flubot infections used spam text messages to trick users into giving device permissions, including access to the Android Accessibility service. This access allowed Flubot to hide in the background and launch malicious tasks throughout a compromised device.
Remember, hackers get remarkable results aiming urgent messages at potential targets. Whether it’s a pop-up window, smishing, vishing, or phishing – urgency, fear, and concern work. After all we’re only human, and that’s what hacker’s love to exploit. A healthy dose of skepticism is always recommended to keep malware like Flubot and countless others from finding a home on our Android devices.
Keep up to date: Sign up for our Fraud alerts and Updates newsletter
Want to schedule a conversation? Please email us at advisor@nadicent.com



Comments