Relentless Ransomware Attacks Against Education Still Rising
- Admin
- Oct 2, 2022
- 2 min read
Published: September 20, 2022 on our newsletter Security Fraud News & Alerts Newsletter.

Whether K-12 or higher education, schools continue to be a ripe target for ransomware attacks. It’s safe to say it’s not a fleeting hacking trend when for years now, colleges, universities, and K-12 have faced relentless ransomware attacks and the devastating fallout that results. Sophos’ State of Ransomware in Education 2022 finds an average 60% increase in attacks against the education sector, up from 44% the prior year.
It’s costly for schools to bolster their security to avoid ransomware and other cyberattacks. Sadly, most education budgets don’t provide enough for the needed improvements and deciding to pay the ransom is the other less desirable and pricey option.
Ransom Payments Ain’t Cheap
Although the FBI maintains paying a ransom demand only encourages more attacks, most schools still prefer paying the ransom for the decryption key that restores their data. But with cybercriminals in charge, there’s no guarantee they’ll keep their word. In fact, you should assume this and the risks that come with it when making this decision.
Sophos finds paying an education institute’s ransom gets just 61% of the hijacked data restored. They also reveal schools themselves pay an average of $1.97 million after a ransomware attack, while individual victims caught-up in the attack pay an average of $905,000. Either way, hacker’s get a lucrative payday.

It Ain’t just Data being Stolen
The fallout from ransomware attacks can cost much more than a ransom payment and lost data. School network interruptions from an attack also prevent students from accessing school resources. It disrupts their ongoing education, academic research, and other resource needs. How long the data standoff lasts depend on both the hacker and the hacked.
If preventing ongoing education isn’t enough to get a ransom paid, hackers also threaten publishing the victim’s stolen data to increase their odds of a ransom payment. That means data that can destroy reputations, including that of the academic institution, is at risk of public exposure. Releasing highly sensitive PII of the many individual victims whose data they now control is an added option.
While there isn’t a guaranteed way to prevent data from being released if a ransom is not paid, you can avoid paying a ransom by making sure all systems are regularly backed up. This goes for the operations data as well as at home on your personal laptop, mobile device, or whatever you use. Backup drives are not expensive, especially in comparison to paying a ransom. Other options include cloud backups and USB sticks. Whatever you choose, make sure to keep those backups safe and secured off the internet so they cannot be compromised by an attack.
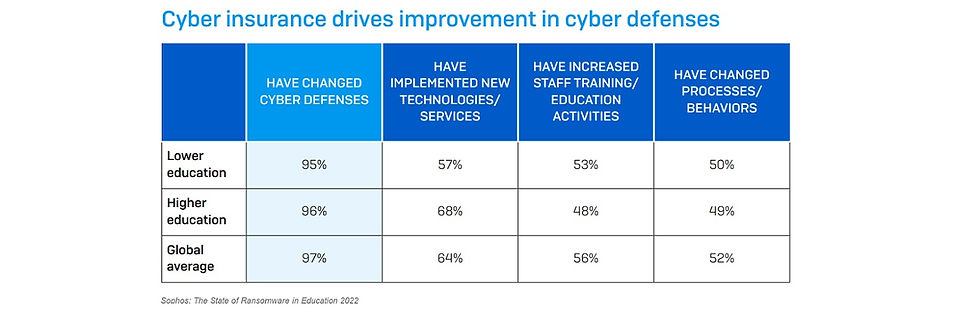
The answer to why education is such a soft target for these attacks, according to the principal research scientist at Sophos, isn’t complicated. He believes the reason why is “They're prime targets for attackers because of their overall lack of strong cybersecurity defenses and the goldmine of personal data they hold…” The only real guarantee is if things stay as they are, increased ransomware attacks against the education sector will continue.
Class dismissed!
Keep up to date: Sign up for our Fraud alerts and Updates newsletter
Want to schedule a conversation? Please email us at advisor@nadicent.com



Comments