Arizonians Duped Out Of $30M In BEC Scams
- Admin
- Jun 5, 2021
- 2 min read
Published: May 28, 2021 on our newsletter Security Fraud News & Alerts Newsletter.

Urgency. That word is important when it comes to BEC (business email compromise) attacks. Like the FBI’s latest urgent warning about another outbreak of BEC affecting businesses in Arizona. According to the Agency, the damages due to BEC totaled $30 million in losses among the AZ business community last year. That’s a 30% spike in losses from the prior year. On a national level, the FBI reports that last year, BEC fraud totaled $1.8 billion in losses to U.S. companies. The FBI finds that BEC is the number one scam in AZ, and unfortunately, it’s just one state out of many falling prey to these costly scams.
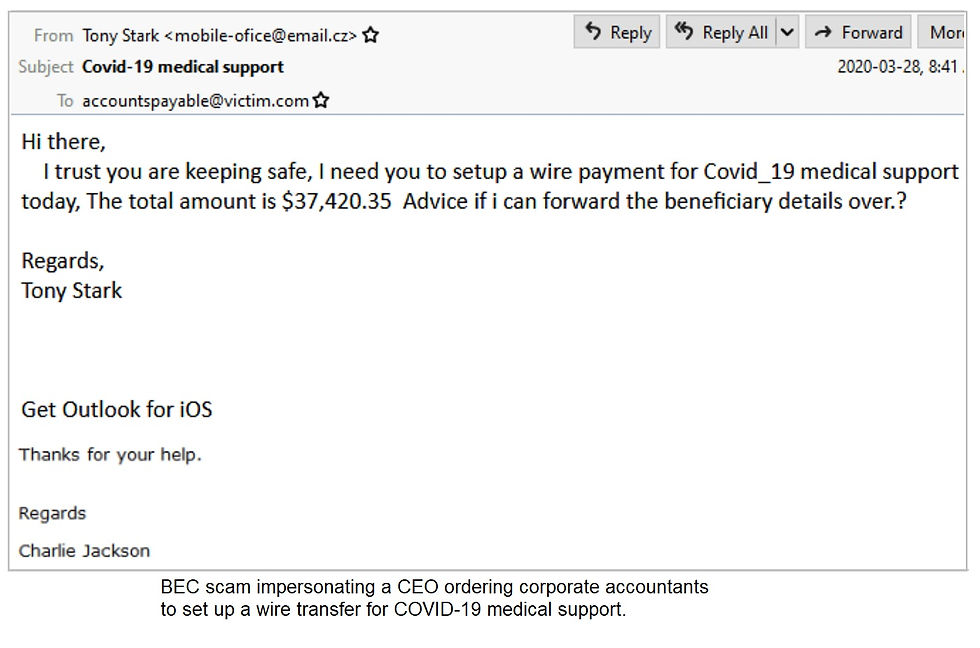
A Look at BEC Fraud
Like many types of cybercrime, BEC’s use email phishing as the lure. In particular, BEC uses social engineering tactics to laser-target recipients. Names, titles, and email addresses are readily available on the dark web, the company Facebook page, LinkedIn, and other platforms. Emails are sent to employees involved with finances, especially those who make wire transfers. Fraudsters pose as someone higher-up in the company or as a trusted vendor, and they typically send “urgent” emails to the target for a large wire transfer. The attacker provides “new” account information for the transfer – one that goes directly into their own account. Once done, the money is gone and a company, wherever it may be, has just been victimized by a BEC.

Doing Due Diligence
Below are actions any business could and should take to minimize the risk of BEC fraud. In particular, those who can make wire transfers should know BEC tactics. If you believe you’re a victim of a BEC scam, the FBI urges contact with their Internet Crime Complaint Center at ic3.gov.

Look for any grammatical errors or odd phrasing. English may not be the hacker’s primary language, or grammar and spelling is not their strong point
Be especially aware of any email language using urgency or other pressure designed to get the BEC target to act quickly
Use multifactor authentication (MFA) or 2FA (two-factor authentication) to help protect email and other accounts from being used for BEC and other cybercrimes
Always confirm a wire transfer with at least one other employee, and never use contact information provided in the email. A CEO would always prefer being asked to verify a wire transfer rather than pay for a scam
Always verify any change in an account number or payment procedures, preferably in person or by other direct contact
Keep up to date: Sign up for our Fraud alerts and Updates newsletter
Want to schedule a conversation? Please email us at advisor@nadicent.com


Comments