Don't Get Hooked Updating That Security Certificate
- Admin
- May 8, 2022
- 2 min read
Published: April 23, 2022 on our newsletter Security Fraud News & Alerts Newsletter.

As if it isn’t difficult enough to determine if a website is legitimate or not, a new phishing technique is going to be keeping us all on our toes now. Cybercriminals are trying to trick website visitors into believing a security certificate for a site needs to be updated before going forward with viewing the site contents. Instead, it’s a nasty surprise waiting behind that update click.

Criminals use our own typing against us. We all make typos when entering a web address from time to time. And criminals know this, so they purchase domains that are a typo away from the actual domain. All they have to do now is sit and wait for someone to misspell a domain and land on their scam website. This almost zero-effort scam called Typosquatting and it is obviously gaining an amazing amount of traction.
Security certificates are used to help us all determine if it’s safe to enter information into a website. Normally, they are indicated by an https:// preceding the website name. Often, the text before the domain name turns green if it’s deemed secure. There also should be a lock icon indicating a secure site. As mentioned before, anyone can buy a security certificate and put it on a website and criminals are doing just that. And it’s becoming harder to determine a safe website for this reason. In this latest case, they are trying to get users to click a link to update a security certificate, but what happens is one of two malware variants gets downloaded to the devices; Mokes or Buerak. These install a backdoor a hacker can use to go back later and capture screenshots, retrieve audio and video files, and steal files among other dastardly things. It also can disguise its activities using encryption.
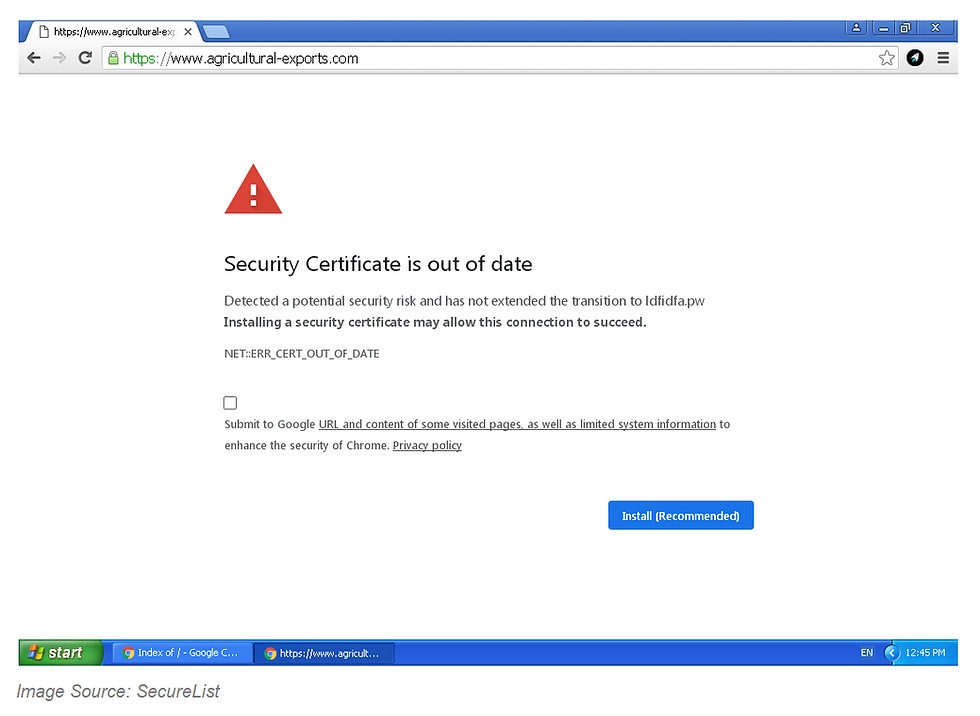
The dialogue that appears notifies the user that the security certificate is out of date. While it is not an unusual dialogue to see if an actual certificate is outdated, it is abnormal to be asked to update a certificate oneself. That’s because it’s the responsibility of the certificate owner to keep that up-to-date. So, if you do see such an option, don’t click it. It very well could be malware.

Also be sure to check for the signs of a secure site mentioned above before entering anything into a site that could be used against you or your organization. While doing those checks, take a look to make sure the website name is spelled correctly in the browser. Domain jacking is not uncommon these days and criminals are always looking for ways to take advantage of your typos by using typosquatting. If there is any doubt of a website's authenticity, don't go any further. Close it out.
Kaspersky reported finding this phishing method and found it on a variety of sites including on a zoo website and an e-commerce site selling parts for vehicles. They found infections dating back to January of this year.
Keep up to date: Sign up for our Fraud alerts and Updates newsletter
Want to schedule a conversation? Please email us at advisor@nadicent.com



Comments